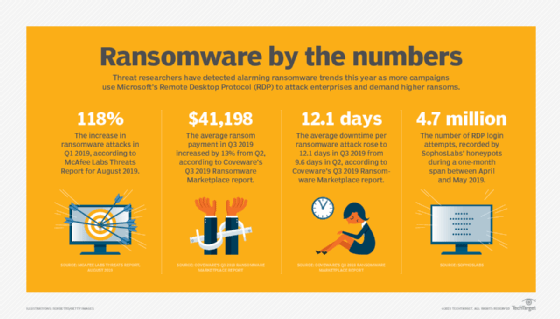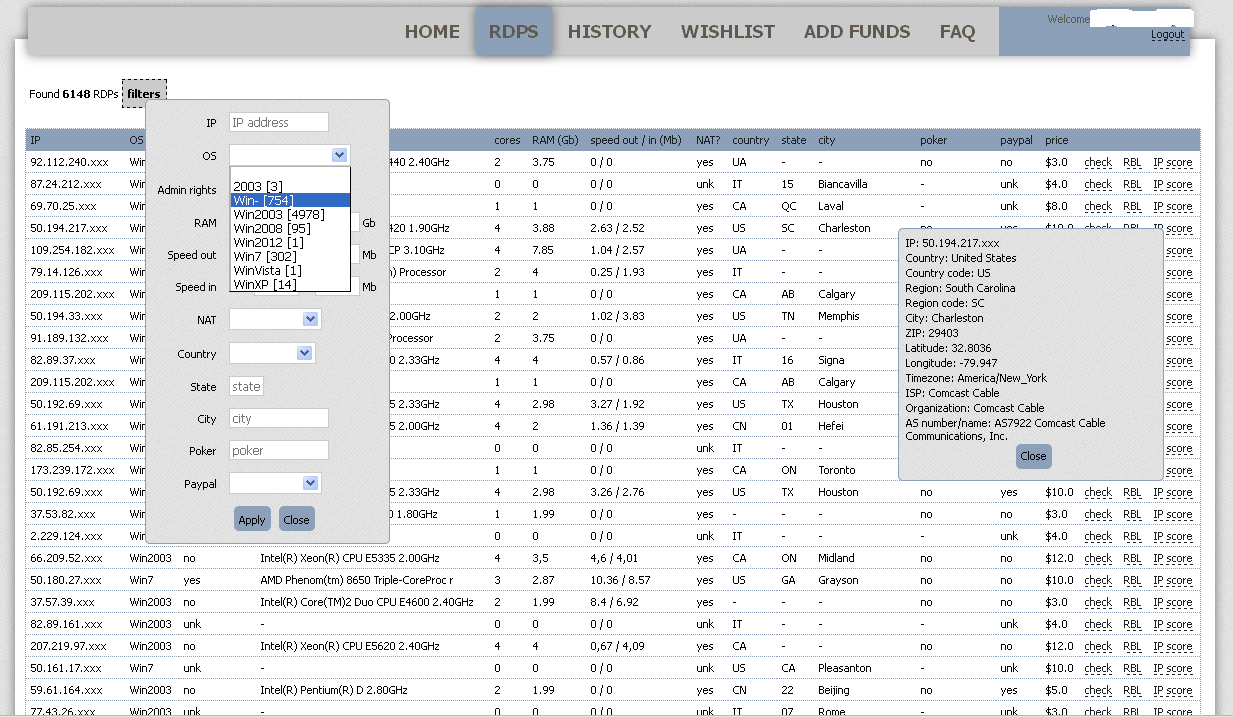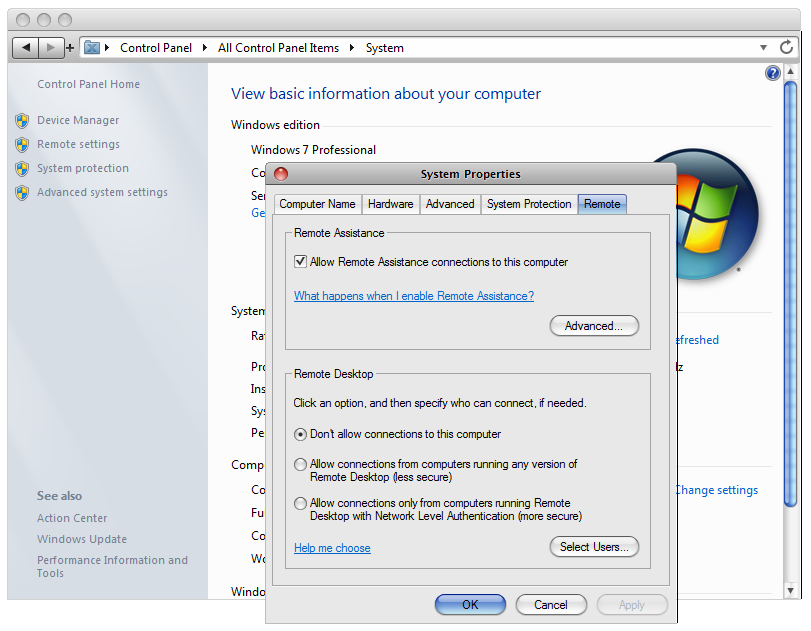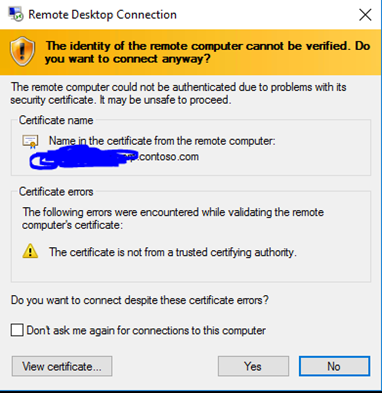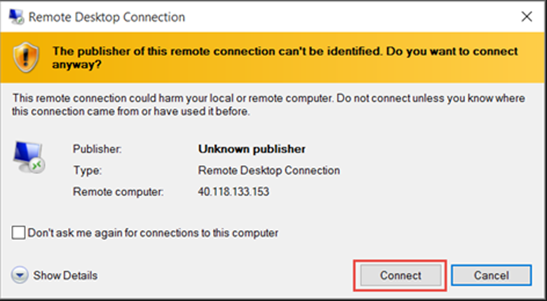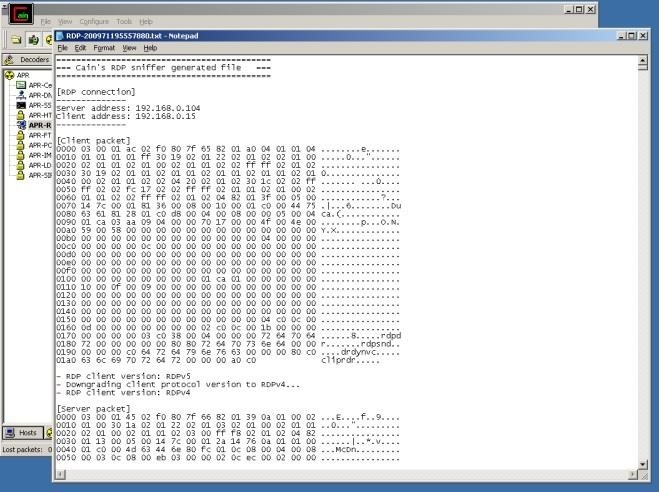
Hack Like a Pro: How to Hack Remote Desktop Protocol (RDP) to Snatch the Sysadmin Password « Null Byte :: WonderHowTo
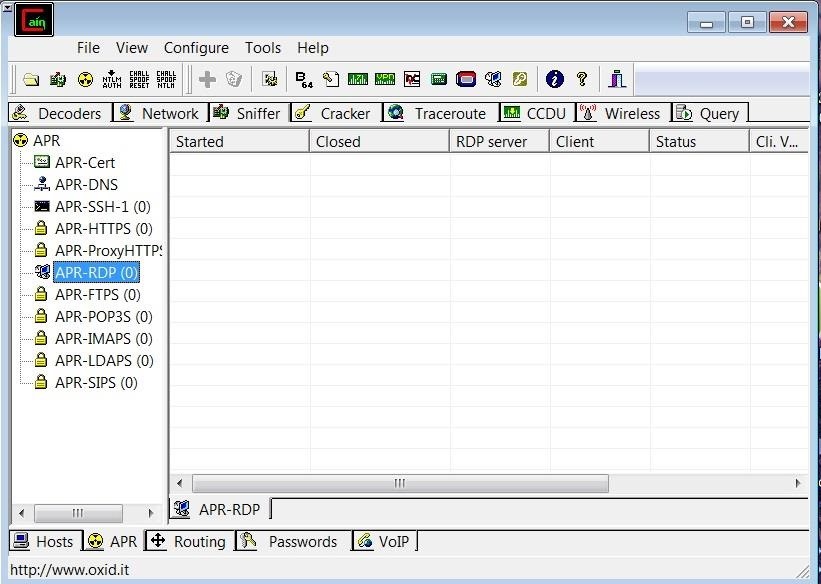
Hack Like a Pro: How to Hack Remote Desktop Protocol (RDP) to Snatch the Sysadmin Password « Null Byte :: WonderHowTo

Hack Like a Pro: How to Hack Remote Desktop Protocol (RDP) to Snatch the Sysadmin Password « Null Byte :: WonderHowTo

Big Jump In Remote Desktop Attacks?! Watch How Hackers Do It And Protect Your Computers Now! - YouTube
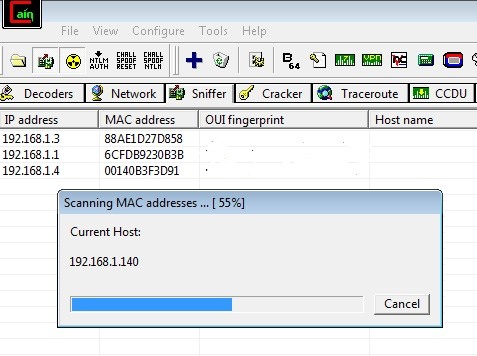
Hack Like a Pro: How to Hack Remote Desktop Protocol (RDP) to Snatch the Sysadmin Password « Null Byte :: WonderHowTo