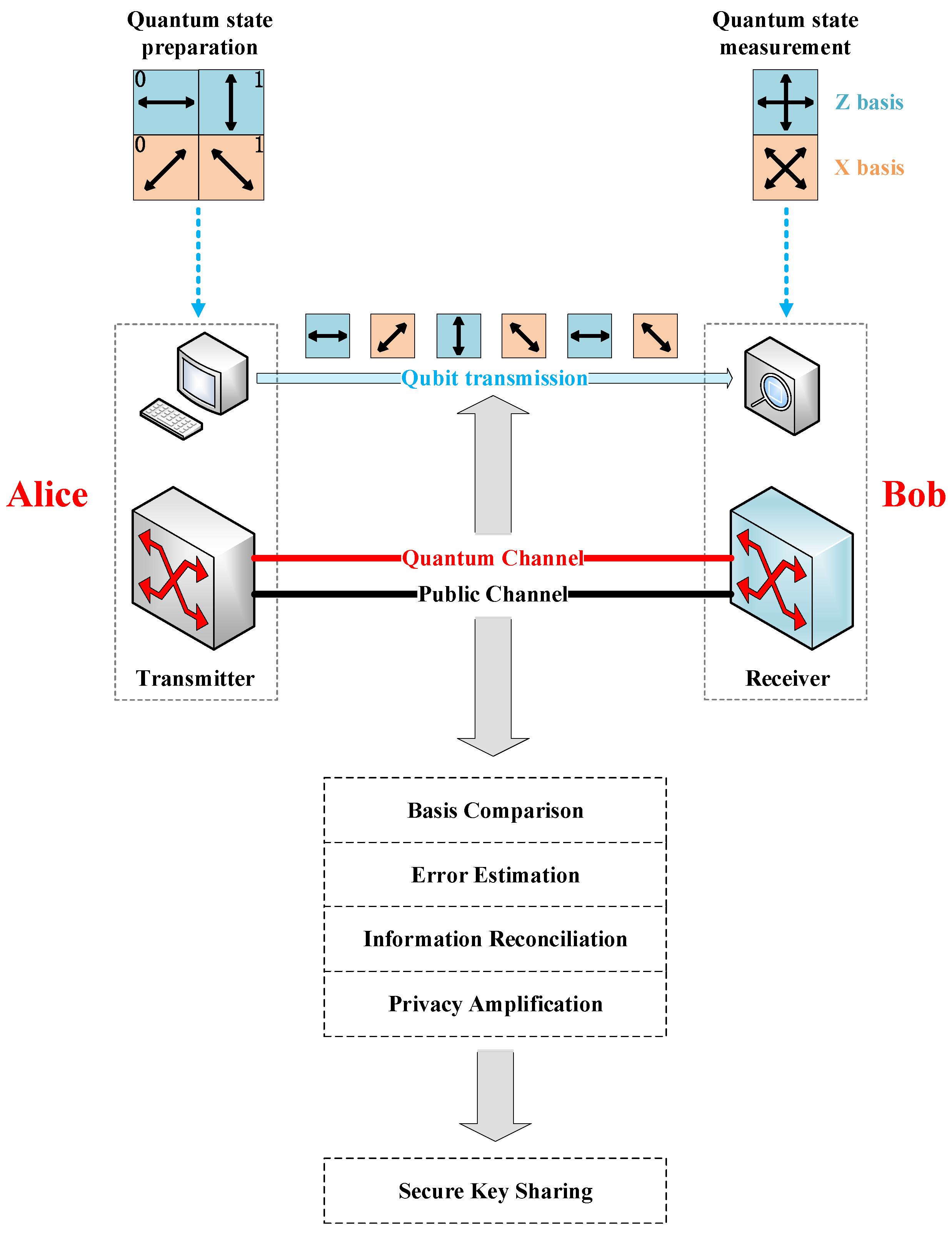
Entropy | Free Full-Text | A Resource-Adaptive Routing Scheme with Wavelength Conflicts in Quantum Key Distribution Optical Networks

The procedure of accelerating length-compatible privacy amplification... | Download Scientific Diagram

High-speed and Large-scale Privacy Amplification Scheme for Quantum Key Distribution | Scientific Reports
![PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5ab3cb538f80f4bbf539103464fe597ba2d93a7c/1-Figure1-1.png)
PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar
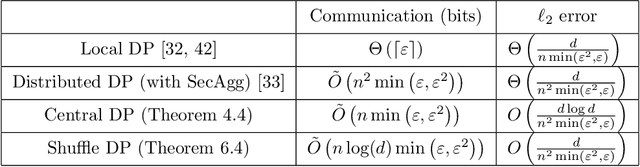
Privacy Amplification via Compression: Achieving the Optimal Privacy-Accuracy-Communication Trade-off in Distributed Mean Estimation: Paper and Code - CatalyzeX
All optical metropolitan quantum key distribution network with post-quantum cryptography authentication

Vitaly 🇺🇦 Feldman on X: "IMO the most significant recent development in privacy preserving data analysis are systems and models that use an anonymizing shuffler. However their formal analysis was rather involved
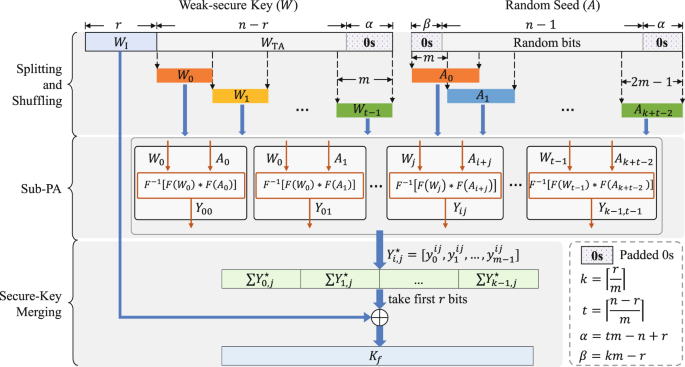
High-speed and Large-scale Privacy Amplification Scheme for Quantum Key Distribution | Scientific Reports
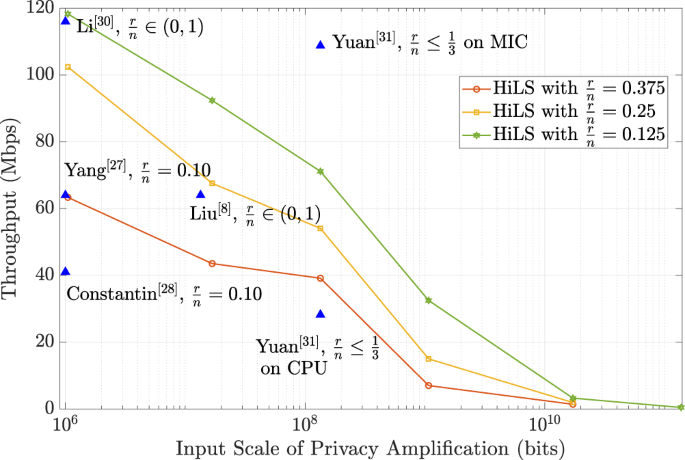
High-speed and Large-scale Privacy Amplification Scheme for Quantum Key Distribution | Scientific Reports

PDF) QKD secrecy for privacy amplification matrices with selective individual attacks | Nicola Laurenti - Academia.edu

PPT - Randomness Extraction and Privacy Amplification with quantum eavesdroppers PowerPoint Presentation - ID:4846836

Matteo Sordello, Zhiqi Bu, Jinshuo Dong · Privacy Amplification via Iteration for Shuffled and Online PNSGD · SlidesLive
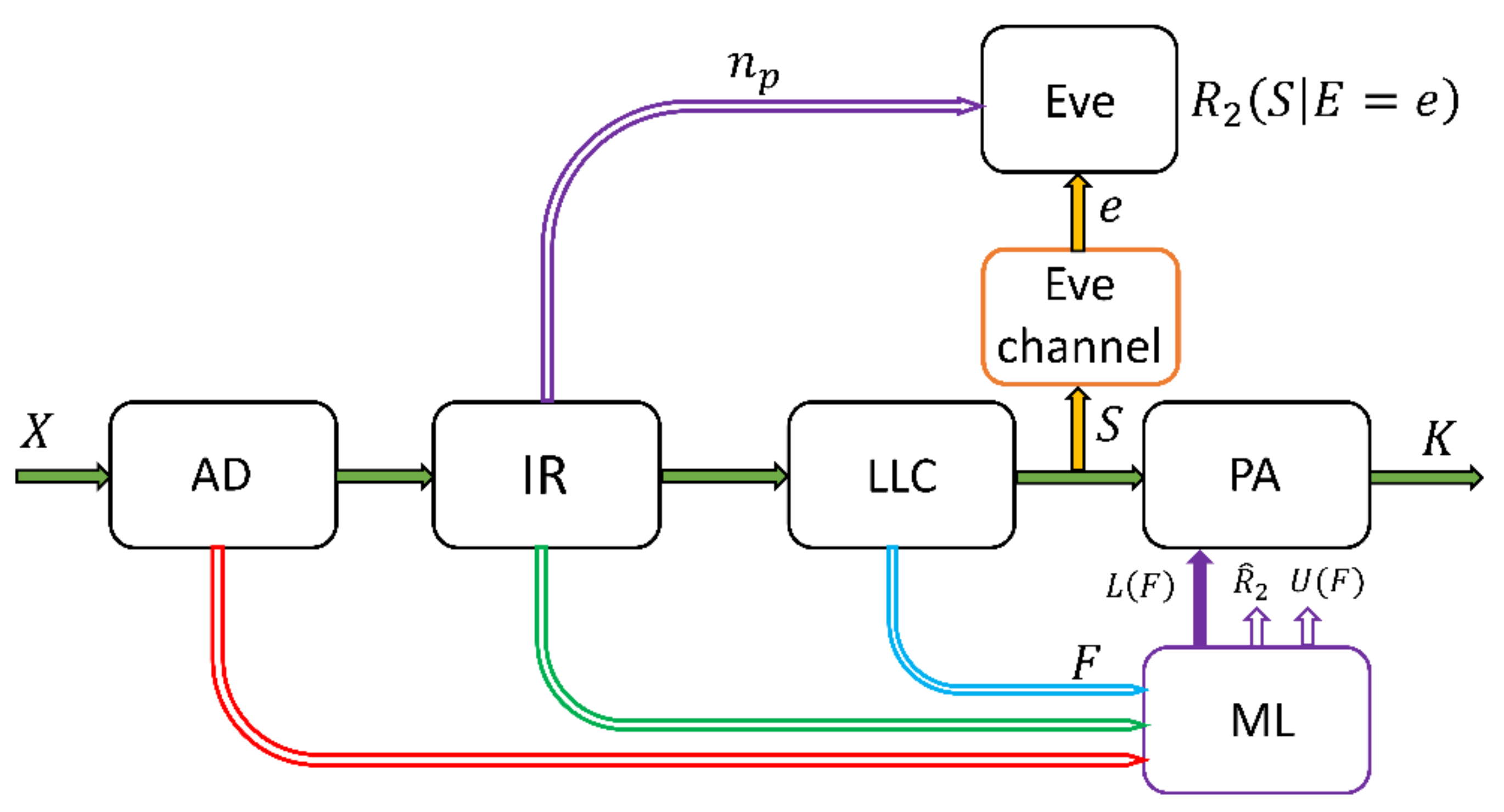





![PDF] Privacy Amplification via Random Check-Ins | Semantic Scholar PDF] Privacy Amplification via Random Check-Ins | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a86aa46da4bcf1daef2e88b7656b7c8477db8e0f/2-Figure1-1.png)





